Projects
Badges Earned
Class project requiring us to present on artificial intelligence as it relates to cybersec
This presentation seeks to provide a comprehensive an exensive explanation on various types of artificial intelligence. We go over what artificial intelligence large language models are and how they work. We also explore privategpt, which is a popular pdf reader. Additionally we talk about code copilots such as github code copilot and how it works. Then we try to illustrate how someone can jailbreak out of chatgpt censorship to answer any question.
This video showcases PrivateGPT, Github Copilot, and ChatGPT.
Class project requiring us to present a tool created for pentest we chose Nmap and Hydra
In this video, my team and I go over nmap and hydra. We explain the use cases for these tools and provide a comprehensive overview into both tools. Subjects range from features and uses, stealth scan and its benefits, increasing attack surface with version detection, to using vulnerability scanning databases. My group and I also go through the wizard for hydra and list various examples. Finally we end by providing a demonstration against metasploitable virtual machine using Kali Linux.
This video showcases nmap and hydra
Class project requiring us to present a tool or service related to virtualization
This presentation seeks to provide a comprehensive an exensive explanation on what hypervisors are. We go over topics such as significance in modern computing environments, economic impact and efficiency, hypervisor roles and types, type 1 usage, type 2 usage, differences between type 1 and type 2 and management of resources in host machines. This presentation is done with a group of 5 of my peers within the californiat state polytechnic university of pomona for the Masters of Science in Information Security.
This video showcases type 1 and type 2 hypervisors
Class project requiring us to present a tool created for pentest we chose SET
In this video, my team and I go over the social-engineer toolkit (SET) we begin with a broad overview of what the purpose of the tool is and some of the special features it contains. Later we go over the interface and walk through some theoretical scenarios where the tool can be used. Finally, we demonstrate an attack as proof of concept. The learning objective here is to learn how the tool works and when the tool should be used. Intent is everything, this tool was made for ethical hacking.
This video showcases an social engineering tool that can launch phishing websites, develop phishing emails, and create malicious hardware.
Class project requiring us to present a tool or service related to business management.
This presentation seeks to provide a comprehensive intuitive way of looking at today’s identity management technologies and how they function. By critically analyzing and comparing on-premises, hybrid, and fully cloud based solutions and focusing on the benefits of cloud identity management or Identity as a Service (IDaaS). The subject that will be explored will include the features associated with cloud identity management as well as the challenges that plague this organizational technology.
This video showcases identity management specifically cloud-based.
Class project requiring us to present a comprehensive audit report for a company.
In this audit project we chose a designated area of IT to audit and presented our findings. I chose to audit in the area of information security management. My audit encompassed various domains, such as information security operations management and information security technology management. These domains examine processes associated with governance, policy, monitoring, implementation, selection, and maintenance. We created slides and executive summaries to simulate a real world auditing experience.
This video showcases an information security management audit using the ISACA framework.

Beginning my graduate level courses at California Polytechnic State University, Pomona.
After graduating from California State University of San Bernardino I have chose to continue my advance degree in Cybersecurity.
Undergrad projects Bellow
These are some of my projects during my undergraduate degree at California State University of San Bernardino.
Class project requiring us to build an Enterprise Network with virtual machines.
In this video, my team and I go over what we worked on for the Spring semester of 2023 in our Enterprise Network class. Professor Nestler, our class instructor, provided us with a cyberlabs environment containing 9 virtual machines that we then configured to communicate with one another. Each team had a task to complete. It took us a lot of effort and a lot of dedication. Ultimately, the class was a difficult one, but we made sure to get it done.
This video showcases an enterprise network. We go over networking, email servers, and web servers, including products and services.
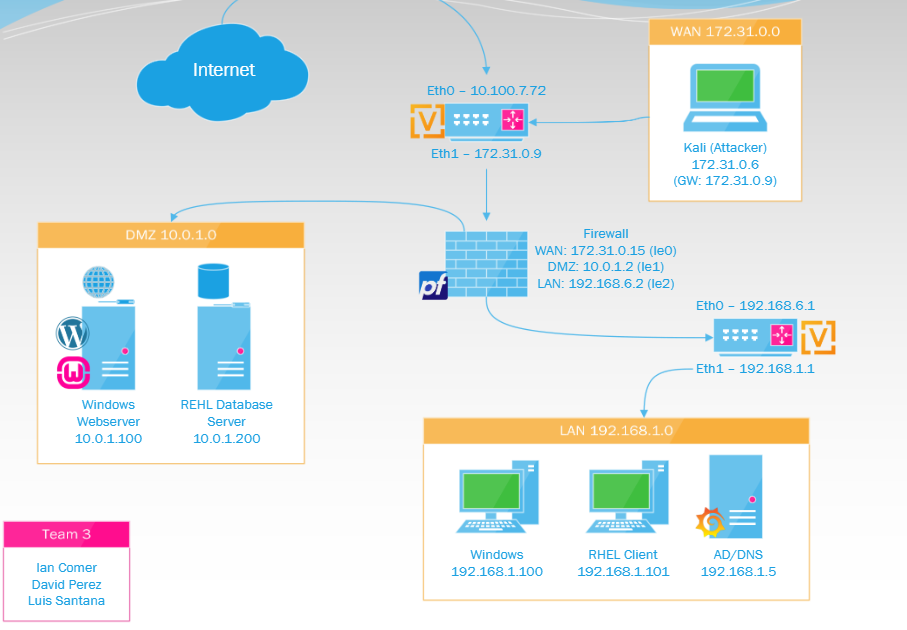
Network Topology
I GRADUATED!
B.S Information Systems and Technology Cybersecurity Concentration Class of 2023 (Magna Cum Laude Honors)
Class project requiring us to creating a podcast describing a pentesting tool: Burp Suite
In this video we go over features found in Burp Suite, we give a comprehensive introduction then we do an overview of the many tools within the program. Finally we end by creating a virtual environment with an attacker machine and a broken web application. The main goal of this project is to describe the pentesting tool in detail this way individuals who are interested in the tool can understand what it does and what it doesn’t do.
This video show cases Burp Suite, its various tools within it and then a practical attack on a web server.
Class project podcast describing the future of cloud services/applications
In this video we go over multiple cloud services and applications, we start by describing what they are and then describing their use. At the end of the segment we make a forecast about the future of said service and application. In the introduction I make sure to point out the basics of what cloud is, the benefits and the challenges that cloud faces. Then I show case Artificial Intelligence specifically pointing out generative AI.
This video showcases cloud services and applications, AI as a service.
In this paper I look into TLS 1.2 and TLS 1.3. I discuss the weaknesses of both and the strengths. I describe the processes of establishing a secure connection between client and server. Furthermore, I specify ciphers currently in use and those ciphers that are discontinued. Even more, my paper explains symmetric and asymmetric encryption methods. I end by explaining the new, old, and upcoming key exchange algorithms.
This paper contains information on TLS 1.2 and TLS 1.3, DH, RSA, DHECC, and QKD.
Volunteered for Chaffey + Cal Poly CyberSecurity Fair Project October 26th
Professor Nimri charged us with the task of completing some videos showcasing vulnerabilities and how to patch them. In this video I show some exploits. I also show how to configure your settings for routers and such for individuals to get a visual representation of how hacks are conducted. Granted the hacks shown here are not very advanced even so if nothing else remember that default factory settings are not the most efficient.
This video showcases Kali Linux exploits, how to take advantage of browser saved passwords etc.
C++ and BluePrint Character Movement.
What type of cybersecurity person would I be if my first aspiration wasn’t to become a game developer? Like everyone did at one point I wished to create games for a living. I learned Unreal Engine 4 to be able to try my hand at creating something fancy. I created a third person character movement model. I also used some pretty cool 3d modeling software named Blender (though I did want to learn Maya at one point) Enjoy this simple illustration.
I realized game designing/developing wasn't for me after making a survival game. Its really cool and all but its just not for me.
In this paper I look into FISMA what it is and what it does. I also talk about frameworks necessary for an organization to be compliant with the law governing federal data management such as the Risk Management Framework (RMF) created by the National Institute of Standards and Technology (NIST) I take a systemic approach and explain the steps require for top down organization privacy and security structuring.
This paper contains information on FISMA, NIST, RMF, SP 800-53, FIPS199, SP 800-37r2, SP 800-37.
The professor forgot to give us the VM login
This one was a funny one. My professor gave us access to a pentesting lab, however, he forgot to give us the login information for the kali linux machine. Most individuals decided to wait until he got back to us with the information. I thought I’d give logging in a try, after all, the pentest lab was created for that very reason – to hack.
Needless to say, I decided to include this clip in the 2020 Cal Poly Cybersecurity and Awareness Fair presentation.
Saving your password saves you time but...
Very interesting take on saving your password. You often see those little dots when your browser automatically fills in the password field but what you don’t know is that those dots can be changed to the characters of your password. Here’s a little dose of reality. The scary part is that you need little to no knowledge about html to deploy this extremely basic attack.




